HOWTO: Amazon Inspector with Terraform
I have been playing around with Terraform for the last 2 months or so, and I really enjoy working on it. The entire approach to…

I have been playing around with Terraform for the last 2 months or so, and I really enjoy working on it. The entire approach to Infrastructure as Code, especially the modular parts, are not only powerful, but also extremely intuitive and easy-to-use, once you get used to the HCL (Hashicorp Configuration Language).
Today, I’d like to detail a simple use-case where Terraform is used as a way to provision and configure an Amazon EC2 Server (I’ll be using Ubuntu in this example) and configure Amazon Inspector to scan said server for security vulnerabilities once provisioned.
While this appears to be a seemingly simple use-case, I didn’t find too many good examples detailing this implementation. Before, I dive in, some intro:
What is Amazon Inspector?
Amazon (AWS) Inspector is a service that Amazon provides for its customers on AWS. This service allows you to configure a vulnerability scanner to identify and flag vulnerabilities in your server environment.
In short, Amazon Inspector is a Vulnerability Scanner (similar to Nessus/Qualys/etc) that scans the target server for security vulnerabilities to captures these vulnerabilities in a set of reports that can be used by the DevOps team to patch and remediate as required.
Amazon inspector is an agent-based service, which needs to be deployed on the servers that needs to assess for vulnerabilities. Unlike several vulnerability scanners, Amazon Inspector cannot be run remotely against a target to identify flaws.
Amazon inspector uses “Rules Packages” to identify vulnerabilities against the target packages. These Packages contain different signatures, rules and payloads that would be used to identify security vulnerabilities on the target system. They are, namely:
- Common Vulnerabilities and Exposures (CVE Database) => Popular database of existing vulnerabilities against commonly used software components.
- CIS Benchmarks => Center for Internet Security Hardening Benchmarks for commonly used software components
- Security Best Practices => Specific list of good security practices that one should follow while running servers.
- Runtime Behavior Analysis => Security analysis based on the services deployed on the target EC2 instance. Typically includes Insecure ports and services, Unused TCP ports, Insecure Client protocols, among others.
Details of these Rules Packages can be found here.
Amazon Inspector can be run against specific Linux and Windows Operating System versions and distros. You can find that list here. In addition, Amazon Inspector works only for deployments in specific AWS regions.
A Minimal Example: Terraform and Amazon Inspector
As Amazon Inspector is an agent-based service. You would need to download the agent to the EC2 server(s) that you want to run security assessments against, to identify vulnerabilities. Obviously, when you have a small set of servers, manually installing the agent is not very complex, but when you are running deployments at (massive) scale, you would need automated orchestration to handle this for you, and that’s where Terraform comes in.
In this example, I will use Terraform to provision an Ubuntu 16.X server on Amazon EC2. To use Amazon Inspector, this server needs to be part of a “Resource Group”, that is used by Terraform to identify the specific targets that it would need to be run against. Subsequently, I will generate Amazon Inspector-specific configurations to specify an “Assessment Template” which is Amazonspeak for “configure a set of rules to be run against the target(s)”. Finally, after this has been provisioned, you can actually “run” the assessment, which in this case is 1 hour.
Explanation (for the above):
- In the above code snippet, I am provisioning an AWS EC2 ubuntu instance, using a generated keypair to inject ssh keys into the newly provisioned instance.
- In line 12: I am adding this EC2 server to a tag called “InspectInstances” which I will be using subsequently to run Inspector assessments against (Resource Group)
- Line 15–26: I am downloading and installing the Amazon Inspector agent from an approved source. Consider hash-matching for higher security.
Explanation (for the above):
- In this segment of the instance.tf file, I am initializing a Resource Group that will be used by Amazon Inspector to perform its security scan. (Line 1–5)
- Subsequently, I am adding all the servers in that Resource Group to be targets of my security assessment. Please note that this will only work against servers that have the agents installed.
- Lines 12–23, I am defining an Assessment Template. In this case, my server is hosted in the us-east-1 region. So the rules for CVE, CIS, etc are specific to the region. You can find this list of Amazon Resource Names (arns) here and here
Please note that this code is only for demonstration purposes. I have not added several other security features to the EC2 deployment like VPCs, and more restrictive security groups. That’s beyond the scope of this article
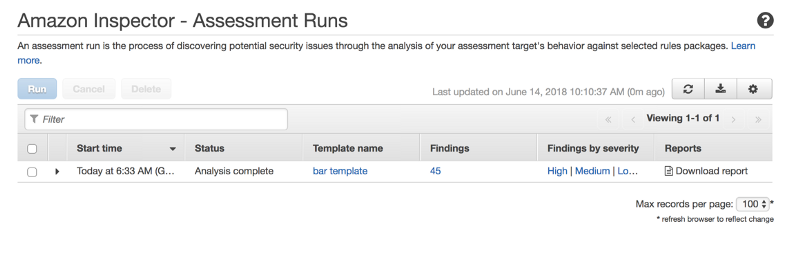
Now, once I run “terraform apply”, I would find that the EC2 server (ubuntu 16) gets provisioned and the inspector agent gets installed in the server.
Subsequently, an Amazon Inspector Assessment also gets provisioned, based on the Resource Group, Assessment Rules and Targets.
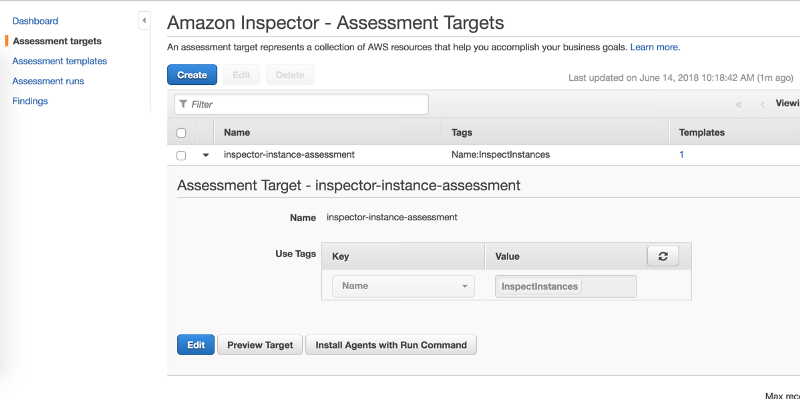
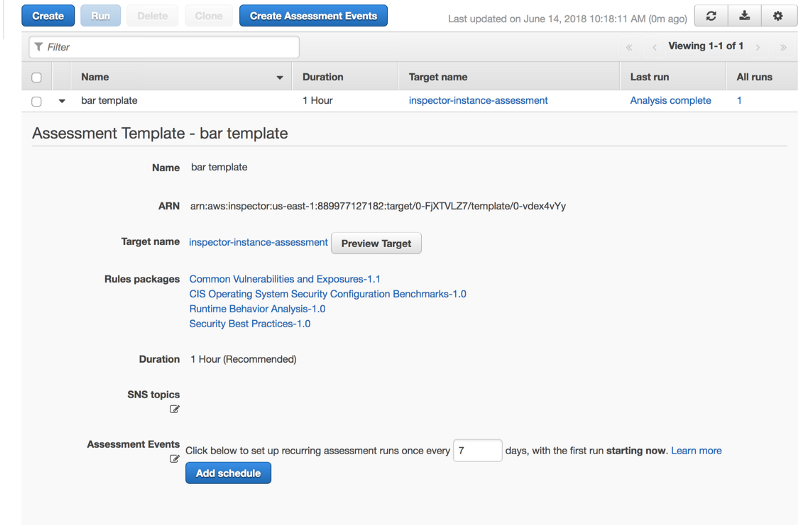
All that remains now is to actually “run” the assessment. Unfortunately, I didnt find any terraform modules that run the assessment for you (I may be wrong). However, since AWS can be completely controlled with its SDK, you can use boto (or equivalent) to invoke the “run_assessment()” function.
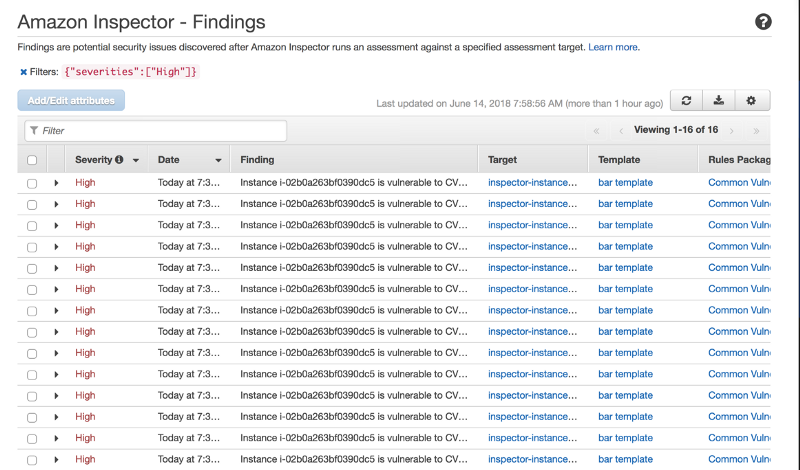
For this example, I manually invoked the “Run Assessment” and these are the example of some of the results
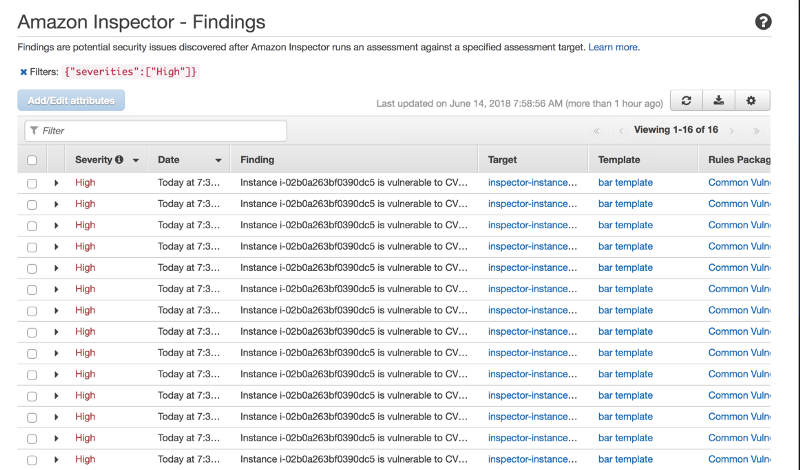
As you can see, Amazon Inspector has identified a number of security issues that I would need to investigate and remediate as required.
Conclusions:
- Amazon Inspector is Vulnerability Scanning Service from Amazon that works in an “agent-based” mode against specific Operating Systems on EC2
- Terraform has comprehensive modules that allow you to not only provision and setup infrastructure on cloud environments, but also invoke APIs related to ancillary services like Amazon Inspector
This content has been made possible by the team at we45. we45 is a focused Application Security and Security Automation Company. Apart from Technical Security Services, we45 offers in-depth training programs on Application Security, Cloud Security, Containers, DevSecOps among others. Contact us at we45.com if you want to know more.
