3 Takeaways from the Qatar National Bank Security Breach
The big story this week is around the “alleged” Data breach of Qatar National Bank (QNB). The attack came as a bolt from the blue with the…
The big story this week is around the “alleged” Data breach of Qatar National Bank (QNB). The attack came as a bolt from the blue with the attackers releasing a massive data-dump of over 1.5GB on the open internet. The file was available for a short while as a zip file that could be downloaded by all who could find it. While it isn’t clear if this is the entire dataset extracted from QNB, the data exposed on the internet is a significant quantum of data that has had the obvious effect. I am sure that customers of the bank would be “running for the hills” as several details concerning customers, especially high-profile customers have been released on the internet, including their account information, financial transfers and so on.
I have had a look at the data dumps from the breach and they are not pretty. Here’s what I think happened and what other companies can learn from this breach.
Poor Data Protection
As per reports, Attackers have definitely used SQL Injection as one of the modes of attack. There have been clear logs from tools like SQLmap that have been run against a Java web application that is querying an Oracle Database. The SQL Injection seems to have been trivially exploited with UNION queries being used to exploit the SQL Injection and extract a ton of data from the back-end Oracle Database.
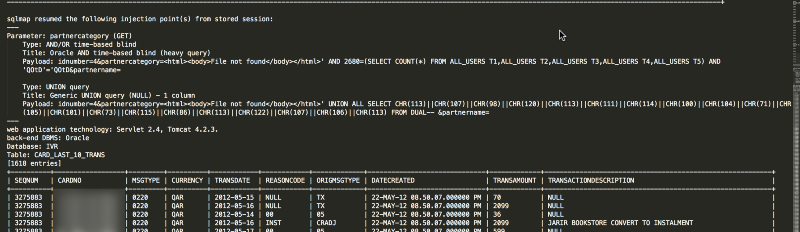
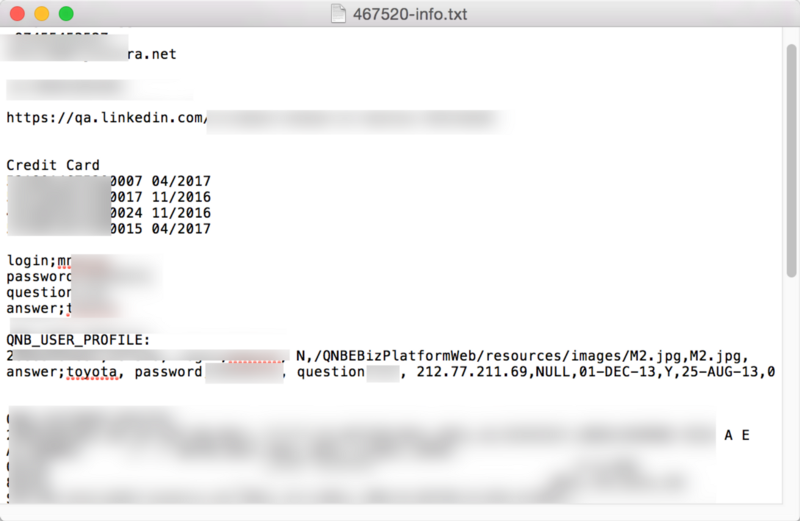
The other thing that obviously stands out is the fact that the card numbers or PANS (Primary Account Numbers) as they are called in the world of payments have been stored entirely in plaintext. Thousands upon Thousands of card numbers across the files have obviously been stored in plaintext by the bank in the database. This is quite a sad state, because the bank has adopted a number of solutions that are supposedly PCI Compliant and may be on the road/already PCI compliant themselves. In any cases, storing the PAN without encryption or other protections is a serious lapse in data security.
In addition, I have found multiple traces of passwords, password questions and password answers stored in plaintext. This is downright vexing to me as it indicates that passwords were in plaintext, as were password questions and answers. All of this information seems to have been extracted from the SQL Injection. The passwords of highly influential members of the press, royal family and large business groups have been released with their photographs, passwords and associated QNB card numbers have been released.
The Power of Application-driven Pivot Attacks
One thing that security professionals like me cry hoarse about is the nature of application-driven pivot attacks. Once someone has compromised then application using an attack like SQL Injection, they typically use that access to pivot and gain access to much. In this attack, the attackers seem to have targeted the Internet Banking application of QNB to perform the SQL Injection and subsequently use this to gain access to their payment switch (Base24) and gain access to account transfer information and possibly even the core banking system.
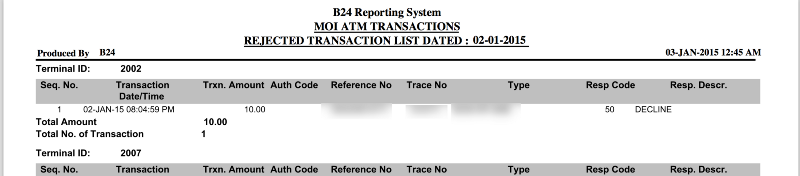
A key requirement for complex IT environments is to ensure seamless security orchestration between different systems, networks and stakeholders. Organizations often tend to miss out on attackers once they are inside the network. With a a typical over-focus on preventive attacks from an external source, organizations miss out on catching attacks when attackers are in the network. In this case, the attackers have had intimate access to the organization’s internal systems including their core banking system, payment switch and its reports, etc.
Where was the monitoring?
I looked around the internet for IT Security jobs at QNB, and they have had several ads out for Information Security personnel with experience in Log Monitoring, SIEM, security management, etc. I can say with little doubt that they probably have an army of security monitoring tools, technologies and people thrown that this problem. Knowing the region, I can say that they probably have deployed some of the most of the most sophisticated network security and monitoring technologies out there. My question is — Where did it all go? An attack like this would have produced a ton of chatter on the network. My team and I use SQLmap and we know that it is not a “stealthy” tool. Its not as if the attackers try to “hide” their tracks. Their approach has been more cudgel than rapier, in that they have made little effort to hide the fact that they were in the network egressing a ton of data from it. I have often observed that network security at these large institutions tends to be a “hygiene” security effort where its essentially done because it has to be done, without much of a purpose or strategy attached to it. While I cannot comment on the quality of the security management and monitoring at QNB, I can say that it was probably not very effective with 1.4 GB or more of data leaving the door completely undetected.
